- Services
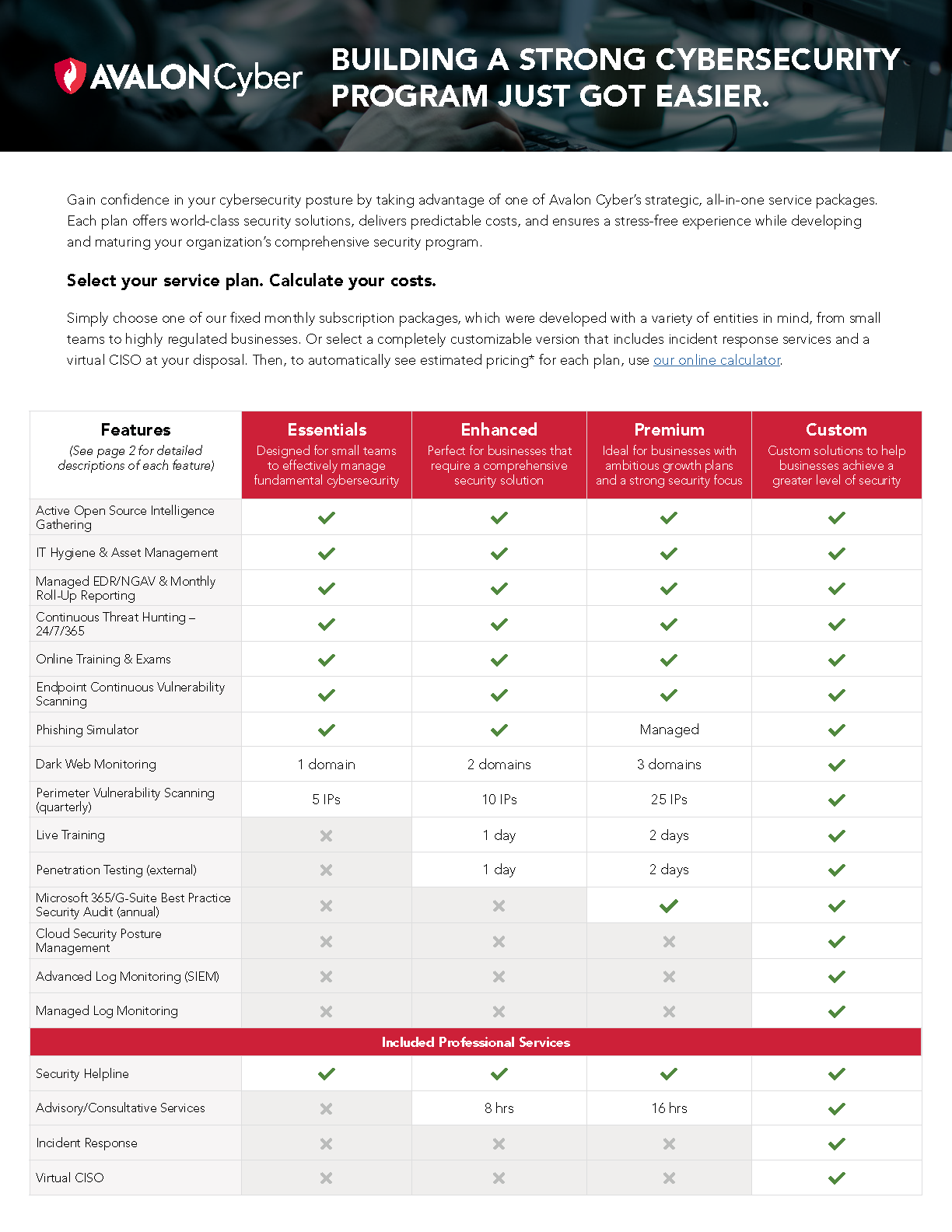
- MDR Cybersecurity Service Plans
- Managed Detection & Response (MDR)
- Managed Extended Detection & Response (MXDR)
- Vulnerability Assessments
- Penetration Testing
- Incident Response
- Incident Response Retainer Program
- Security Advisory Services
- Virtual Chief Information Security Officer (vCISO)
- Microsoft 365 Security Assessment
- Data Breach Review
- Data Breach Notifications
- Dark Web Monitoring
- Phishing Simulation and Training
- Why Avalon Cyber?
- Resources
- Leadership
- Contact Us
- Careers
- Service Plans & Pricing